A massive security hole affecting Mac computers running the latest version of MacOS High Sierra has been discovered.
This is a critical bug that allows anyone on a Mac to log in and change the admin settings - using just the username "root" with no password, according to developer Lemi Ergin, who spotted the bug on 28 November. To test it, attempt to access an administrator's account on an unlocked Mac and then the locked login screen of that Mac after reboot.
Here's everything you need to know about the bug, including who is affected by it and whether there is a fix yet.
How to test for High Sierra 'root' bug
This exploit doesn't require any major hacker skills. And, once in, you can control all administration functions and edit your own permissions. For example, you can give yourself administrator privileges or set up new administration-level accounts or whatever you desire.
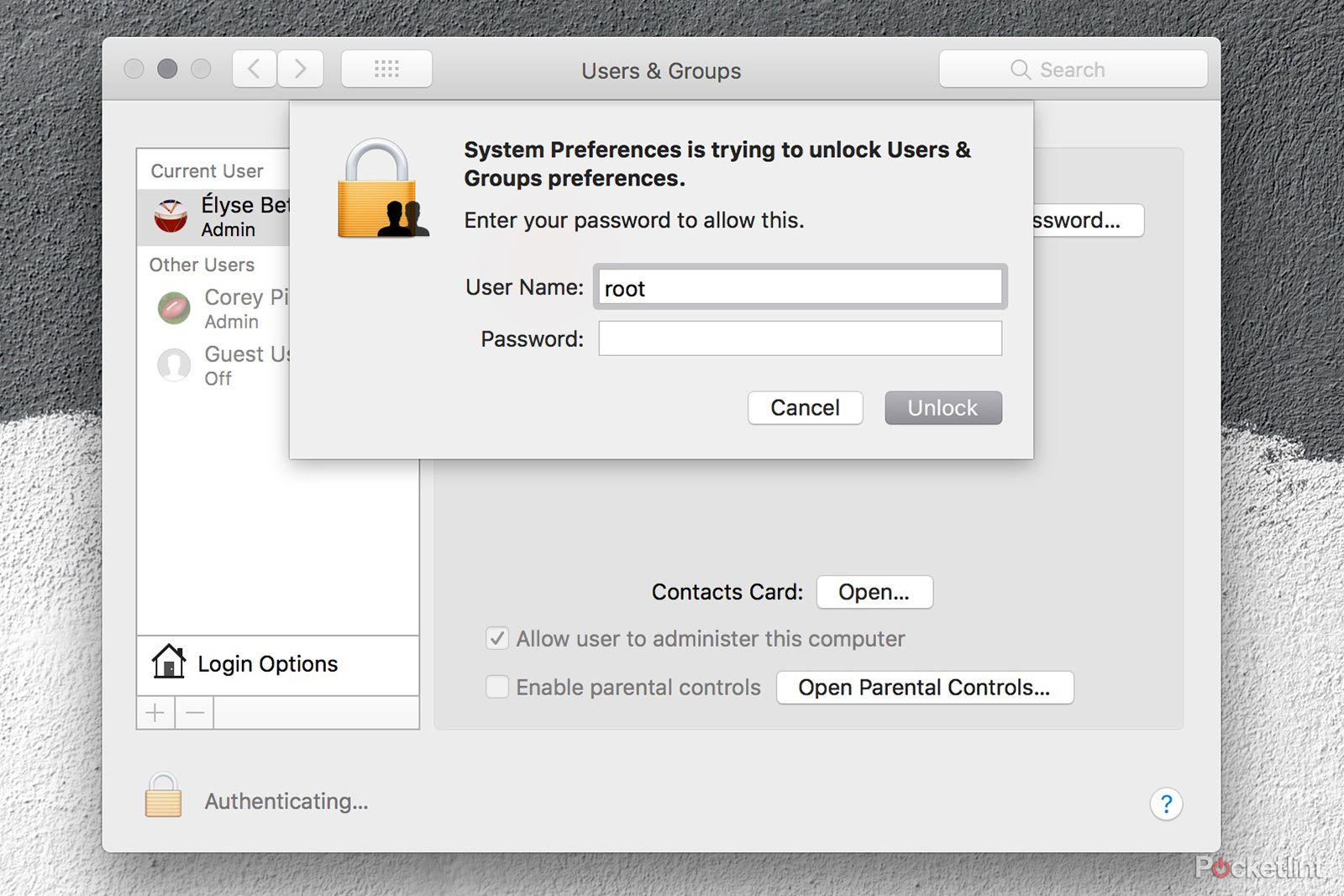
If trying to access an administrator's account:
- Open System Preferences.
- Select Users and Groups.
- Click the lock in the corner.
- In the login field, type "root" as the username.
- Go to the Password field but leave it blank.
- Click unlock.
- At this point, you should have full access.
It also allows for anyone to login to a machine immediately after reboot:
- At the login screen, click "Other".
- Enter "root" again with no password.
- At this point, you should have full admin access from the locked login screen.
- From the account, you'll able to see everything on the Mac.
Who is affected by High Sierra 'root' bug?
Those of us at Pocket-lint who are running older versions of the MacOS operating system weren't able to replicate the bug. We are updating our machines and will report back. However, several users on Twitter, who are running the current version, MacOS High Sierra 10.13.1, and the MacOS 10.13.2 beta, have said they were able to replicate it.
So, the problem seems to exist in the following versions of MacOS:
- MacOS High Sierra 10.13.0
- MacOS High Sierra 10.13.1
- MacOS High Sierra 10.13.2 beta
How to fix High Sierra 'root' bug
Permanent fix
Apple has released a security update, called Security Update 2017-001, for Mac machines running MacOS High Sierra 10.13.1 and later. This is a fix for the critical bug that enables full admin access - with just 'root' as the username and a blank password - on any Mac running MacOS High Sierra. The update is rolling out on the Mac App Store now for MacOS High Sierra users. We suggest installing it immediately.
Temporary workaround
Prior to releasing the security update on 29 November, Apple told Pocket-lint that setting a root password prevents unauthorized access to your Mac. To enable the Root User and set a password, follow the steps on this support page. If a Root User is already enabled, Apple said you should still ensure a blank password is not set by following the steps from the 'Change the root password' section of its support page.
How could this happen?
That's a good question, considering security should be a top priority for every company. However, Apple has admitted it stumbled with this release of MacOS High Sierra. Its security engineers became aware of the issue on 28 November and immediately began working on the update that closed the security hole, Apple told us. It also promised to audit its development process to prevent this from happening again.
"We apologize to all Mac users, both for releasing with this vulnerability and for the concern it has caused," Apple said in a statement.